Testbed
Datasense Device Inventory
Full list:
devices.csv
The dataset testbed consists of a heterogeneous set of network infrastructure, brokers, edge nodes, industrial sensors, cameras, and smart plugs. Each device is uniquely identified by its MAC and IP addresses, and is assigned a descriptive name, role, and type. For sensors, the associated MQTT main topic is also provided, which indicates the stream under which data was published. This detailed inventory allows researchers to understand the roles of devices within the testbed, trace traffic and sensor data back to specific hardware, and correlate network captures with IoT/IIoT telemetry.
The Architecture of Datasense testbed is shown in the Figure Below.
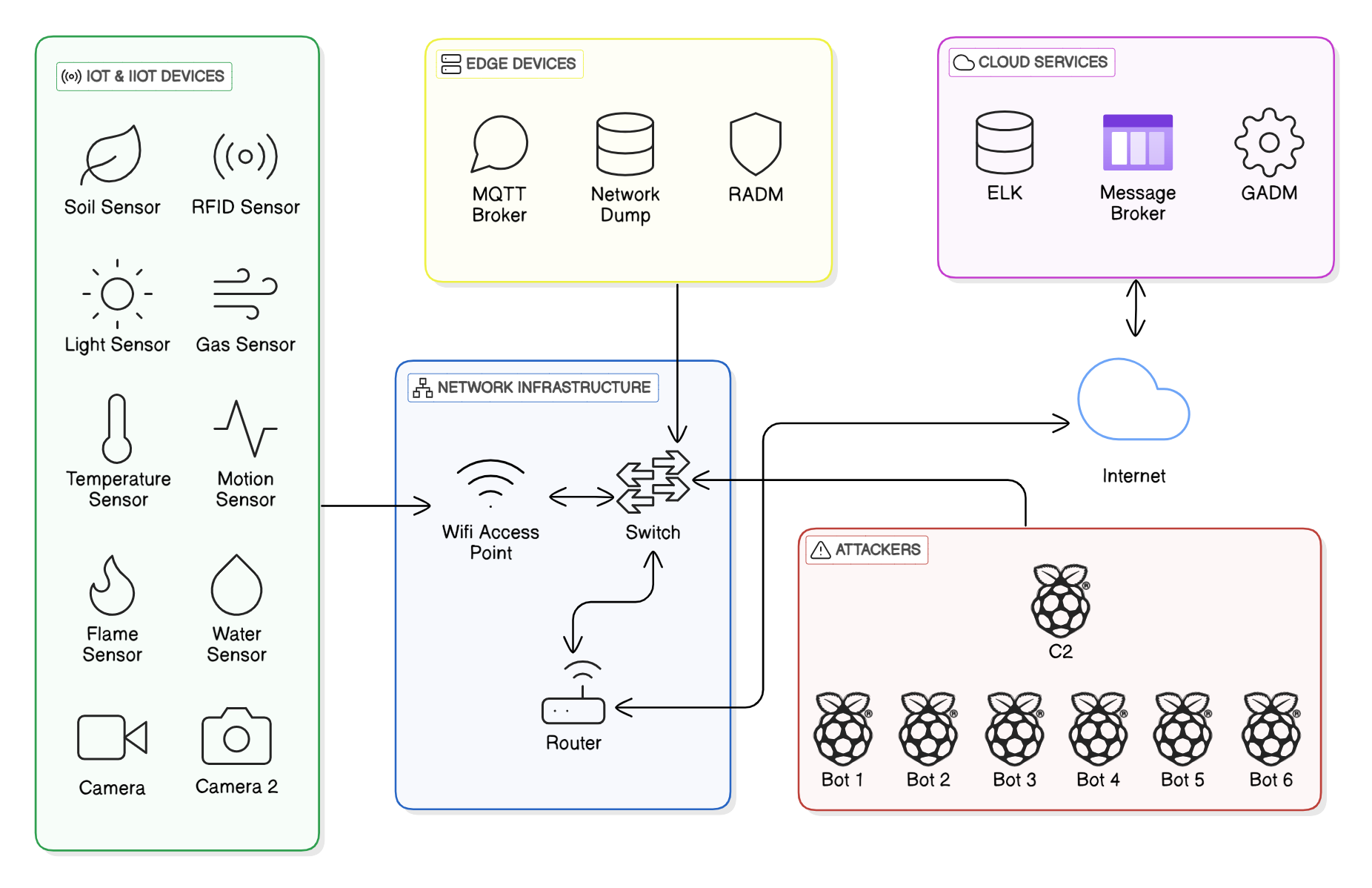
Testbed Devices
| MAC | IP | Device Name | Role | Type | Main Topic |
|---|---|---|---|---|---|
| 28:87:ba:bd:c6:6c | 192.168.1.1 | router | router | network | – |
| dc:a6:32:dc:28:46 | 192.168.1.193 | mqtt-broker | mqtt-broker | raspberry-pie | – |
| dc:a6:32:dc:27:d4 | 192.168.1.195 | edge1 | edge | raspberry-pie | – |
| e0:46:ee:21:56:18 | 192.168.1.200 | switch | switch | network | – |
| 30:de:4b:e2:13:4e | 192.168.1.205 | ap | ap | network | – |
| 08:b6:1f:82:12:30 | 192.168.1.10 | weather-sensor | sensor | sensor | iiot/weather/temp |
| 08:b6:1f:84:66:78 | 192.168.1.11 | water-sensor | sensor | sensor | iiot/water |
| f0:08:d1:ce:cf:0c | 192.168.1.12 | soil-sensor | sensor | sensor | iiot/soil |
| 08:b6:1f:81:d2:cc | 192.168.1.13 | steam-sensor | sensor | sensor | iiot/steam |
| 08:b6:1f:83:25:98 | 192.168.1.14 | gas-sensor | sensor | sensor | iiot/gas/gas |
| f0:08:d1:ce:cf:c8 | 192.168.1.15 | sound-sensor | sensor | sensor | iiot/sound/big |
| 08:b6:1f:82:27:d0 | 192.168.1.16 | vibration-sensor | sensor | sensor | iiot/vibration |
| 08:b6:1f:82:ee:c4 | 192.168.1.17 | ultrasonic-sensor | sensor | sensor | iiot/ultrasonic |
| 8c:aa:b5:8a:a9:b4 | 192.168.1.18 | light-sensor | sensor | sensor | iiot/light/light |
| 08:b6:1f:82:ee:44 | 192.168.1.19 | accelerometer-sensor | sensor | sensor | iiot/acceleration/xyz |
| 08:b6:1f:82:ef:30 | 192.168.1.20 | proximity-collision-sensor | sensor | sensor | iiot/proximity/level |
| 08:b6:1f:82:1c:3c | 192.168.1.21 | motion-sensor | sensor | sensor | iiot/motion |
| 08:b6:1f:82:2b:1c | 192.168.1.22 | rfid-sensor | sensor | sensor | iiot/rfid/check |
| 08:b6:1f:82:ee:cc | 192.168.1.23 | flame-sensor | sensor | sensor | iiot/flame |
| 7c:94:9f:84:71:7e | 192.168.1.50 | yi-camera | camera | camera | – |
| 14:c9:cf:45:3e:ba | 192.168.1.52 | blurams-camera | camera | camera | – |
| 44:29:1e:5c:de:12 | 192.168.1.53 | dekco-camera | camera | camera | – |
| 20:50:e7:f0:0a:04 | 192.168.1.54 | myq-camera | camera | camera | – |
| dc:29:19:95:3a:79 | 192.168.1.55 | geeni-camera | camera | camera | – |
| 00:09:18:6d:73:b9 | 192.168.1.57 | wisenet-camera | camera | camera | – |
| c4:dd:57:15:5c:2c | 192.168.1.80 | plug-all-cameras | smart-plug | plug | – |
| c4:dd:57:0d:f2:76 | 192.168.1.81 | plug-all-rpb | smart-plug | plug | – |
| d4:a6:51:1f:f6:7c | 192.168.1.82 | plug-mqtt | smart-plug | plug | – |
| d4:a6:51:1d:c0:ed | 192.168.1.83 | plug-rfid | smart-plug | plug | – |
| d4:a6:51:22:03:99 | 192.168.1.84 | plug-edge1 | smart-plug | plug | – |
| d4:a6:51:1d:74:3a | 192.168.1.85 | plug-motion | smart-plug | plug | – |
| d4:a6:51:20:91:f7 | 192.168.1.86 | plug-flame | smart-plug | plug | – |
| d4:a6:51:20:0e:3f | 192.168.1.87 | plug-proximity | smart-plug | plug | – |
| d4:a6:51:79:68:75 | 192.168.1.88 | plug-vibration | smart-plug | plug | – |
| 50:02:91:10:ac:d8 | 192.168.1.90 | plug-cameras-yi | smart-plug | plug | – |
| 50:02:91:10:09:8f | 192.168.1.91 | plug-cameras-geeni | smart-plug | plug | – |
| 50:02:91:11:05:8c | 192.168.1.92 | plug-cameras-dekco-blurams | smart-plug | plug | – |
| d4:a6:51:82:98:a8 | 192.168.1.93 | plug-all-sensors | smart-plug | plug | – |
Column Descriptions
-
MAC
The unique Media Access Control address of the device’s network interface. Used to identify devices at the data link layer. -
IP
The IPv4 address assigned to the device within the testbed network (192.168.1.x subnet). -
Device Name
A descriptive name given to the device (e.g.,router,mqtt-broker,light-sensor). This matches the naming convention used in data files and MQTT topics. -
Role
The logical role of the device in the testbed (e.g.,router,sensor,camera,smart-plug,edge,mqtt-broker). Helps clarify the device’s function. -
Type
The hardware or category type (e.g.,network,raspberry-pie,sensor,camera,plug). Distinguishes between infrastructure, compute nodes, IoT sensors, and actuators. -
Main Topic
The MQTT topic (if applicable) under which the device publishes data streams. For non-sensor devices (routers, cameras, smart plugs), this field is empty.
Testbed Device Inventory (Grouped)
1. Network Infrastructure
| MAC | IP | Device Name | Role | Type | Main Topic |
|---|---|---|---|---|---|
| 28:87:ba:bd:c6:6c | 192.168.1.1 | router | router | network | – |
| e0:46:ee:21:56:18 | 192.168.1.200 | switch | switch | network | – |
| 30:de:4b:e2:13:4e | 192.168.1.205 | ap | ap | network | – |
2. Brokers & Edge Nodes
| MAC | IP | Device Name | Role | Type | Main Topic |
|---|---|---|---|---|---|
| dc:a6:32:dc:28:46 | 192.168.1.193 | mqtt-broker | mqtt-broker | raspberry-pie | – |
| dc:a6:32:dc:27:d4 | 192.168.1.195 | edge1 | edge | raspberry-pie | – |
3. IIoT / IoT Sensors
| MAC | IP | Device Name | Role | Type | Main Topic |
|---|---|---|---|---|---|
| 08:b6:1f:82:12:30 | 192.168.1.10 | weather-sensor | sensor | sensor | iiot/weather/temp |
| 08:b6:1f:84:66:78 | 192.168.1.11 | water-sensor | sensor | sensor | iiot/water |
| f0:08:d1:ce:cf:0c | 192.168.1.12 | soil-sensor | sensor | sensor | iiot/soil |
| 08:b6:1f:81:d2:cc | 192.168.1.13 | steam-sensor | sensor | sensor | iiot/steam |
| 08:b6:1f:83:25:98 | 192.168.1.14 | gas-sensor | sensor | sensor | iiot/gas/gas |
| f0:08:d1:ce:cf:c8 | 192.168.1.15 | sound-sensor | sensor | sensor | iiot/sound/big |
| 08:b6:1f:82:27:d0 | 192.168.1.16 | vibration-sensor | sensor | sensor | iiot/vibration |
| 08:b6:1f:82:ee:c4 | 192.168.1.17 | ultrasonic-sensor | sensor | sensor | iiot/ultrasonic |
| 8c:aa:b5:8a:a9:b4 | 192.168.1.18 | light-sensor | sensor | sensor | iiot/light/light |
| 08:b6:1f:82:ee:44 | 192.168.1.19 | accelerometer-sensor | sensor | sensor | iiot/acceleration/xyz |
| 08:b6:1f:82:ef:30 | 192.168.1.20 | proximity-collision-sensor | sensor | sensor | iiot/proximity/level |
| 08:b6:1f:82:1c:3c | 192.168.1.21 | motion-sensor | sensor | sensor | iiot/motion |
| 08:b6:1f:82:2b:1c | 192.168.1.22 | rfid-sensor | sensor | sensor | iiot/rfid/check |
| 08:b6:1f:82:ee:cc | 192.168.1.23 | flame-sensor | sensor | sensor | iiot/flame |
4. Cameras
| MAC | IP | Device Name | Role | Type | Main Topic |
|---|---|---|---|---|---|
| 7c:94:9f:84:71:7e | 192.168.1.50 | yi-camera | camera | camera | – |
| 14:c9:cf:45:3e:ba | 192.168.1.52 | blurams-camera | camera | camera | – |
| 44:29:1e:5c:de:12 | 192.168.1.53 | dekco-camera | camera | camera | – |
| 20:50:e7:f0:0a:04 | 192.168.1.54 | myq-camera | camera | camera | – |
| dc:29:19:95:3a:79 | 192.168.1.55 | geeni-camera | camera | camera | – |
| 00:09:18:6d:73:b9 | 192.168.1.57 | wisenet-camera | camera | camera | – |
5. Smart Plugs
| MAC | IP | Device Name | Role | Type | Main Topic |
|---|---|---|---|---|---|
| c4:dd:57:15:5c:2c | 192.168.1.80 | plug-all-cameras | smart-plug | plug | – |
| c4:dd:57:0d:f2:76 | 192.168.1.81 | plug-all-rpb | smart-plug | plug | – |
| d4:a6:51:1f:f6:7c | 192.168.1.82 | plug-mqtt | smart-plug | plug | – |
| d4:a6:51:1d:c0:ed | 192.168.1.83 | plug-rfid | smart-plug | plug | – |
| d4:a6:51:22:03:99 | 192.168.1.84 | plug-edge1 | smart-plug | plug | – |
| d4:a6:51:1d:74:3a | 192.168.1.85 | plug-motion | smart-plug | plug | – |
| d4:a6:51:20:91:f7 | 192.168.1.86 | plug-flame | smart-plug | plug | – |
| d4:a6:51:20:0e:3f | 192.168.1.87 | plug-proximity | smart-plug | plug | – |
| d4:a6:51:79:68:75 | 192.168.1.88 | plug-vibration | smart-plug | plug | – |
| 50:02:91:10:ac:d8 | 192.168.1.90 | plug-cameras-yi | smart-plug | plug | – |
| 50:02:91:10:09:8f | 192.168.1.91 | plug-cameras-geeni | smart-plug | plug | – |
| 50:02:91:11:05:8c | 192.168.1.92 | plug-cameras-dekco-blurams | smart-plug | plug | – |
| d4:a6:51:82:98:a8 | 192.168.1.93 | plug-all-sensors | smart-plug | plug | – |
6. Cloud
| MAC | IP | Device Name | Role | Type | Main Topic |
|---|---|---|---|---|---|
| 18:66:da:9f:87:4d | 192.168.230.7 | iot-cloud | cloud | server | – |
Cloud note: iot-cloud is logically placed behind the lab router and represents an external/public cloud service used by some devices (e.g., for telemetry forwarding). It is reachable through the router but no attacks were targeted at the cloud node in these experiments; cloud traffic is included only as background/normal communications where present.
7. Attackers
| MAC | IP | Device Name | Role | Type | Main Topic |
|---|---|---|---|---|---|
| e4:5f:01:55:90:c1 | 192.168.1.100 | attacker0 | attacker | raspberry-pie | – |
| dc:a6:32:c9:e6:f3 | 192.168.1.101 | attacker1 | attacker | raspberry-pie | – |
| dc:a6:32:c9:e5:a3 | 192.168.1.102 | attacker2 | attacker | raspberry-pie | – |
| dc:a6:32:c9:e4:c5 | 192.168.1.103 | attacker3 | attacker | raspberry-pie | – |
| dc:a6:32:c9:e5:01 | 192.168.1.104 | attacker4 | attacker | raspberry-pie | – |
| dc:a6:32:c9:e4:aa | 192.168.1.105 | attacker5 | attacker | raspberry-pie | – |
Note: attacker nodes are the machines (Raspberry Pies) used to generate attack traffic in experiments. Their IPs/MACs are included so researchers can reproduce traffic flows and map packet sources in PCAPs.
Note:
attacker0functions as the attack master / command-and-control (C2) node in the testbed. In single-host experiments it generates offensive traffic directly; in distributed experiments (e.g., DDoS, Mirai-style botnet scenarios) it acts as the C2 server that sends attack commands to the other Raspberry Pi attacker nodes (attacker1...attacker5), which then execute the attack payloads. The role includes: command orchestration, parameter distribution (target IP/port, rate, duration), and centralized logging of attack parameters and start/stop timestamps.